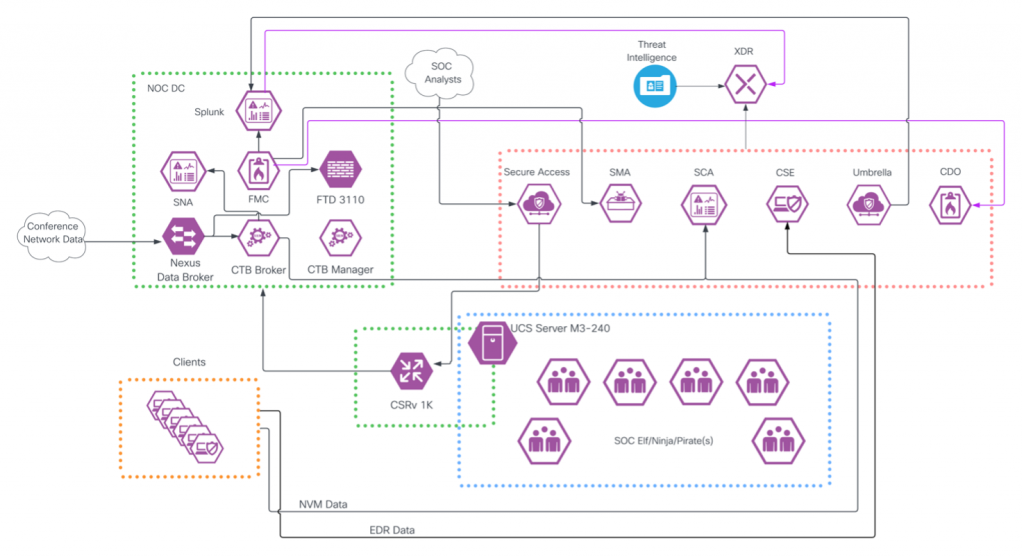
Executive Summary. 1 The Team… 2 Team Leaders. 2 Core Infrastructure and Threat Hunting. 2 Threat Hunting. 2 Build and Operation. 2 SOC Architecture. 2 Cisco Secure Access Enables ZTNA for SOC Admins. 4 Powering XDR with the Cisco Secure Portfolio. 6 Analyst Stories. 9 New Domain Investigations. 9 Mirai Botnet Attempts. 11 Log4j Attempts. […]
Read more





You must be logged in to post a comment.